SQL Injection
A SQL injection attack consists of injection of a SQL query via the input data from the client to an application.
1. Sign in to Cloud One
- Select the Workload Security tile
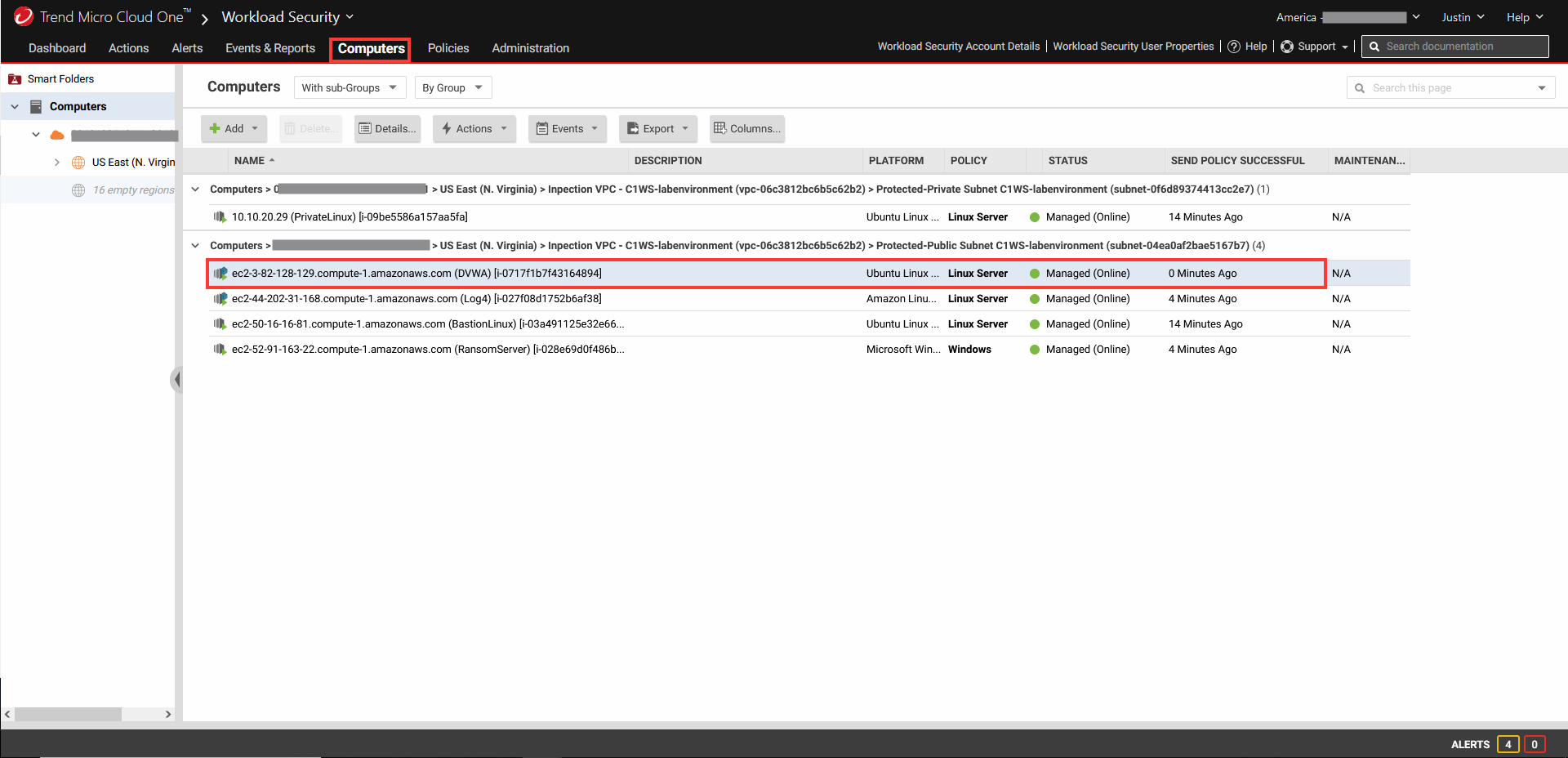
2. Click the Computer tab and locate the DVWA server.
- Click on the DVWA server to open its policy details.
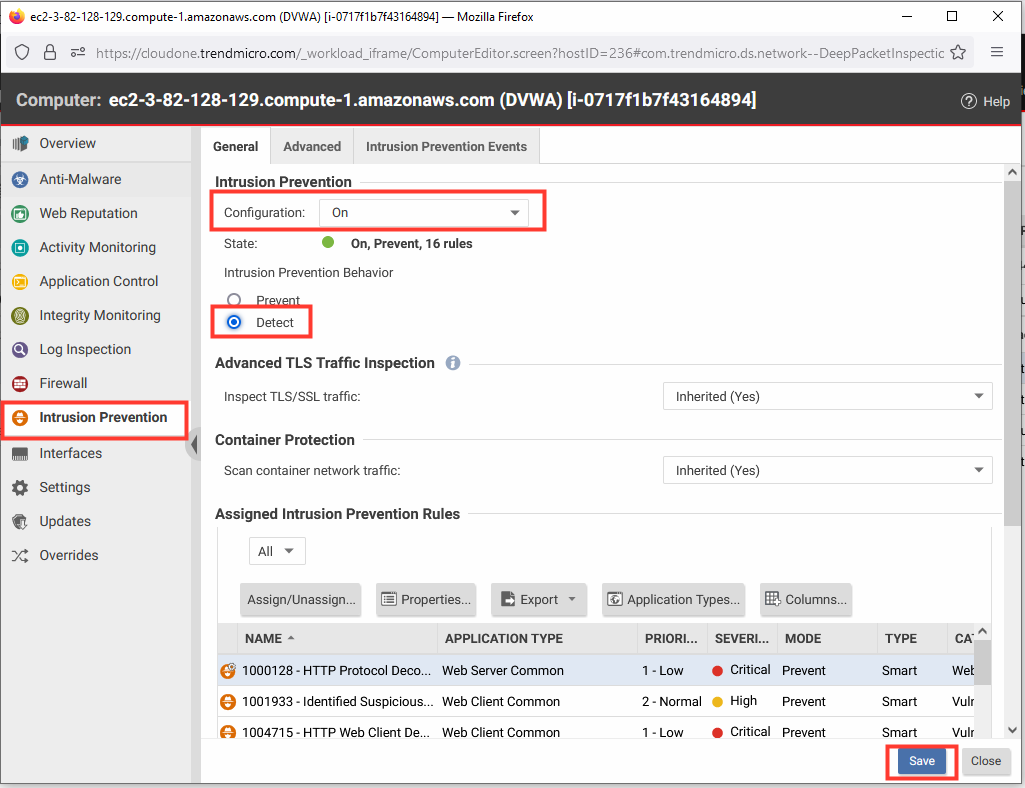
- From the left-hand menu, click Intrusion Prevention.
- Change the default configuration from Inherited to ON.
- Change the IPS behavior to Detect mode.
- Click Save.
3. This application is susceptible to SQL injection attempts. We need to be able to report and protect this security concern.
- Keep the DVWA policy details still open.
- From the left-hand menu, click Intrusion Prevention.
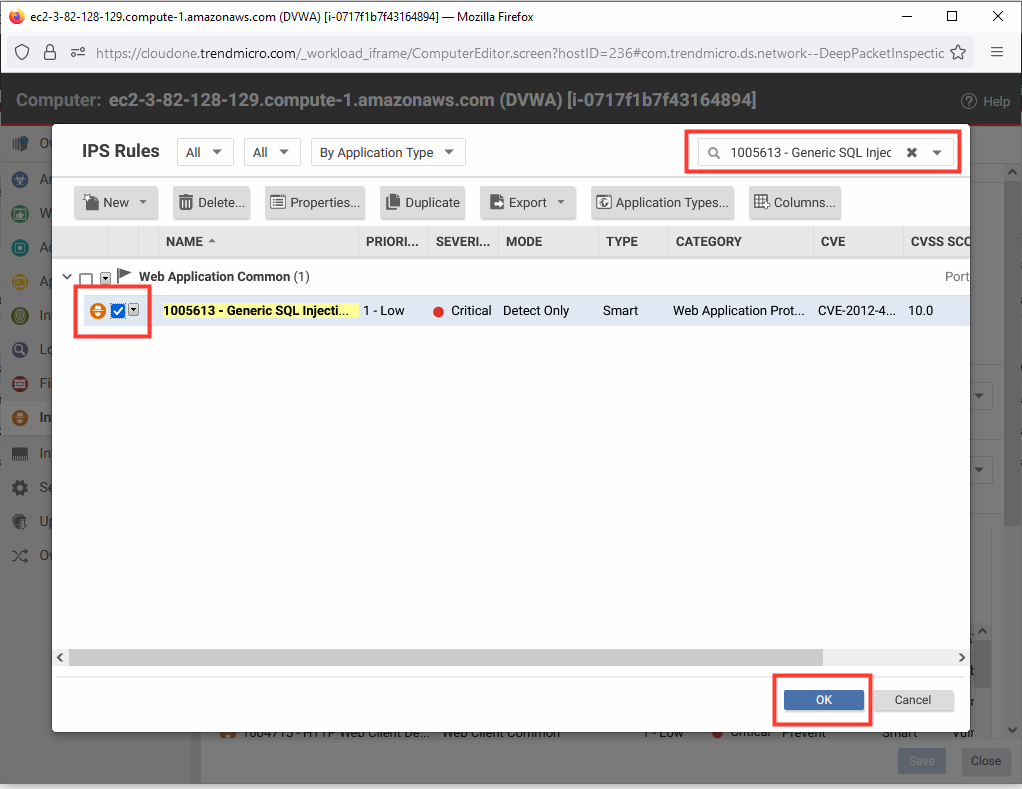
- Click Assign/Unassign to view and add IPS rules specific to this server.
- In the upper right corner, search for the rule
1005613 - Generic SQL Injection Prevention - 2 - Select the checkbox to assign rule 1005613 - Generic SQL Injection Prevention - 2.
- Click OK.
- Click Save and close the policy details window.

4. Now access the DVWA application.
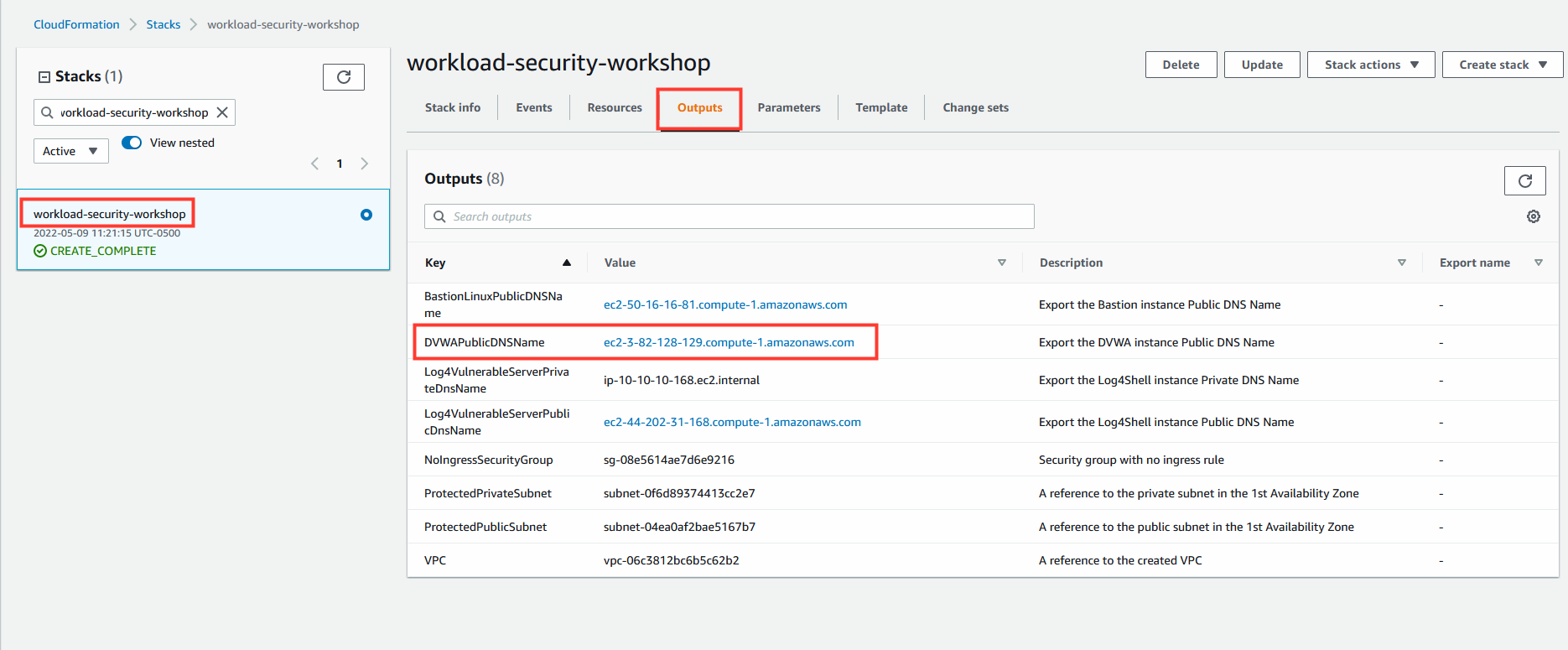
- In the AWS console, navigate to CloudFormation.
- Select the Stack named:
workload-security-workshop. - Select the Outputs tab.
- Copy the value of DVWAPublicDNSName and paste in a new tab of your browser.
5. Access the web application using the Public IP/DNS.
- Remember that it will be over HTTP.
- User:
admin - Password:
password - Login

6. Now that you have successfully logged in, Create/Reset Database.
- Click button: Create/Reset Database
After Create/Reset you will be logged out of the DVWA. Please login again using same credentials from Step 3.

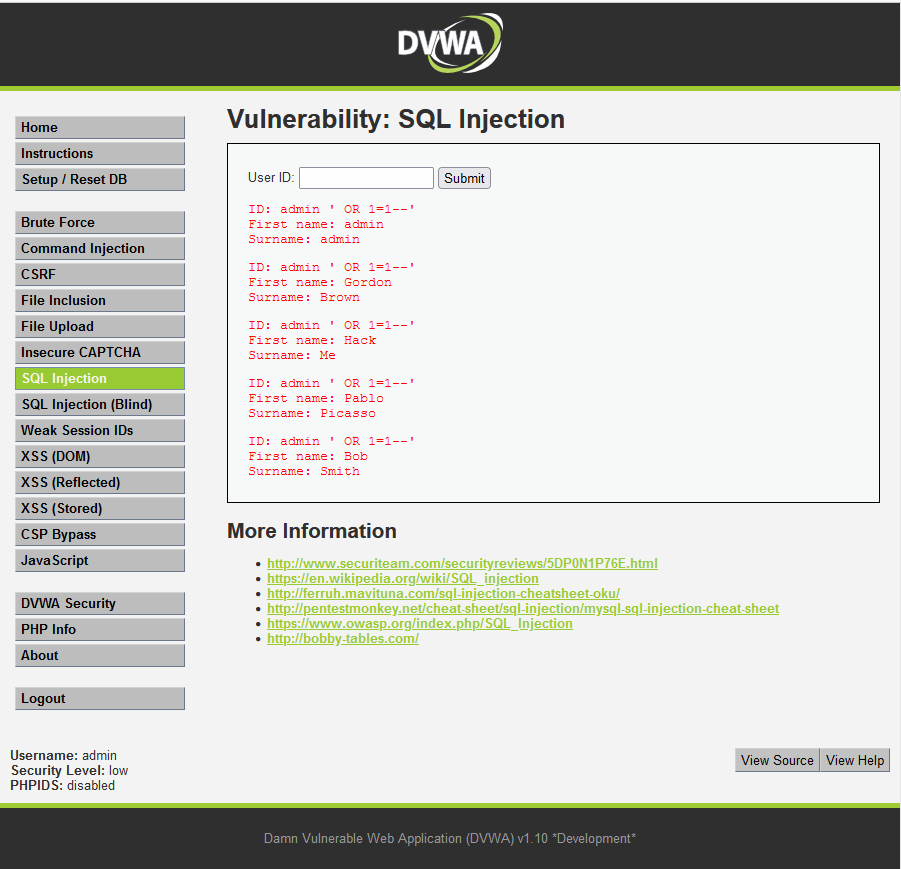
7. DVWA SQL Injection
- Select: SQL Injection
- User ID:
admin ' OR 1=1 --'

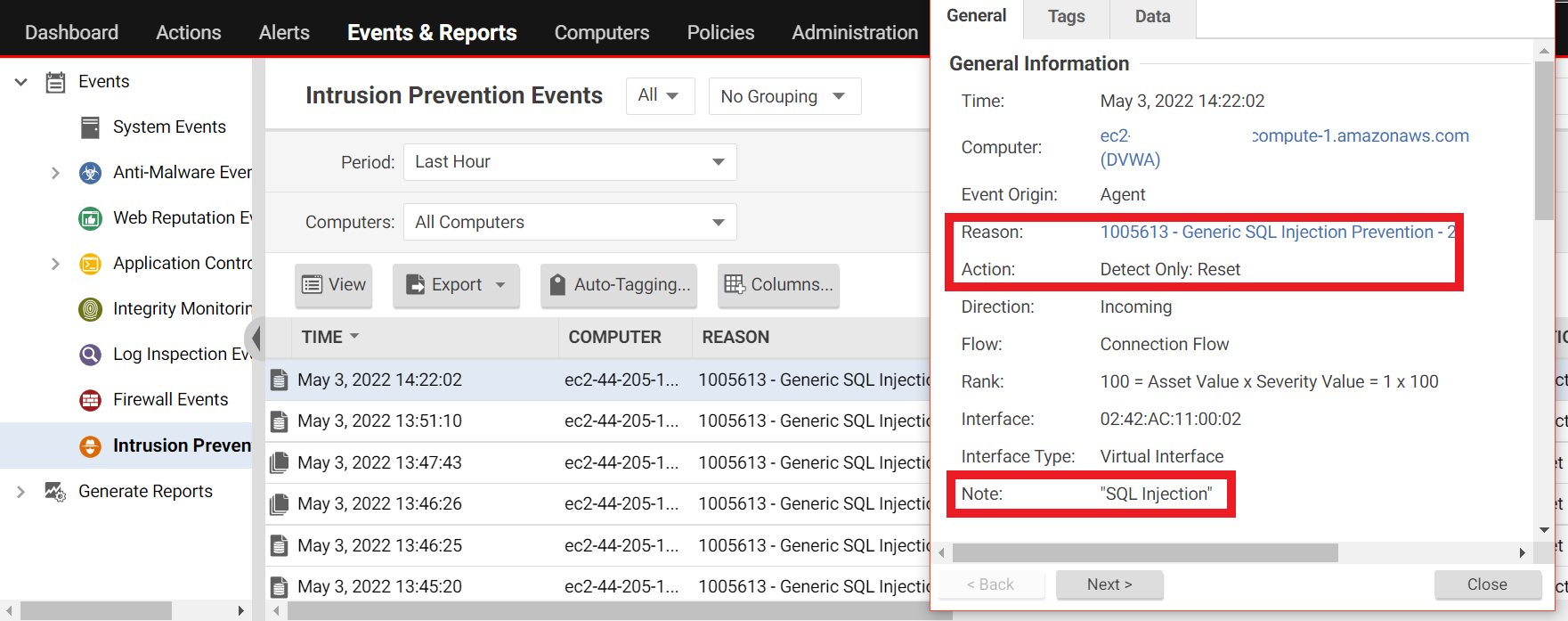
8. Go back to the Workload Security Console.
- Click on Events & Reports tab.
It may take a few minutes for the detection and events to appear on the console (~6 min).

9. Prevent future SQL injection attempts by returning the IPS module to Prevent.
- Click the Computers tab and locate the DVWA server.
- Click on the DVWA server to open its policy details.
- From the left-hand menu, click Intrusion Prevention.
- Change the IPS behavior to Prevent mode.
- Click Save.


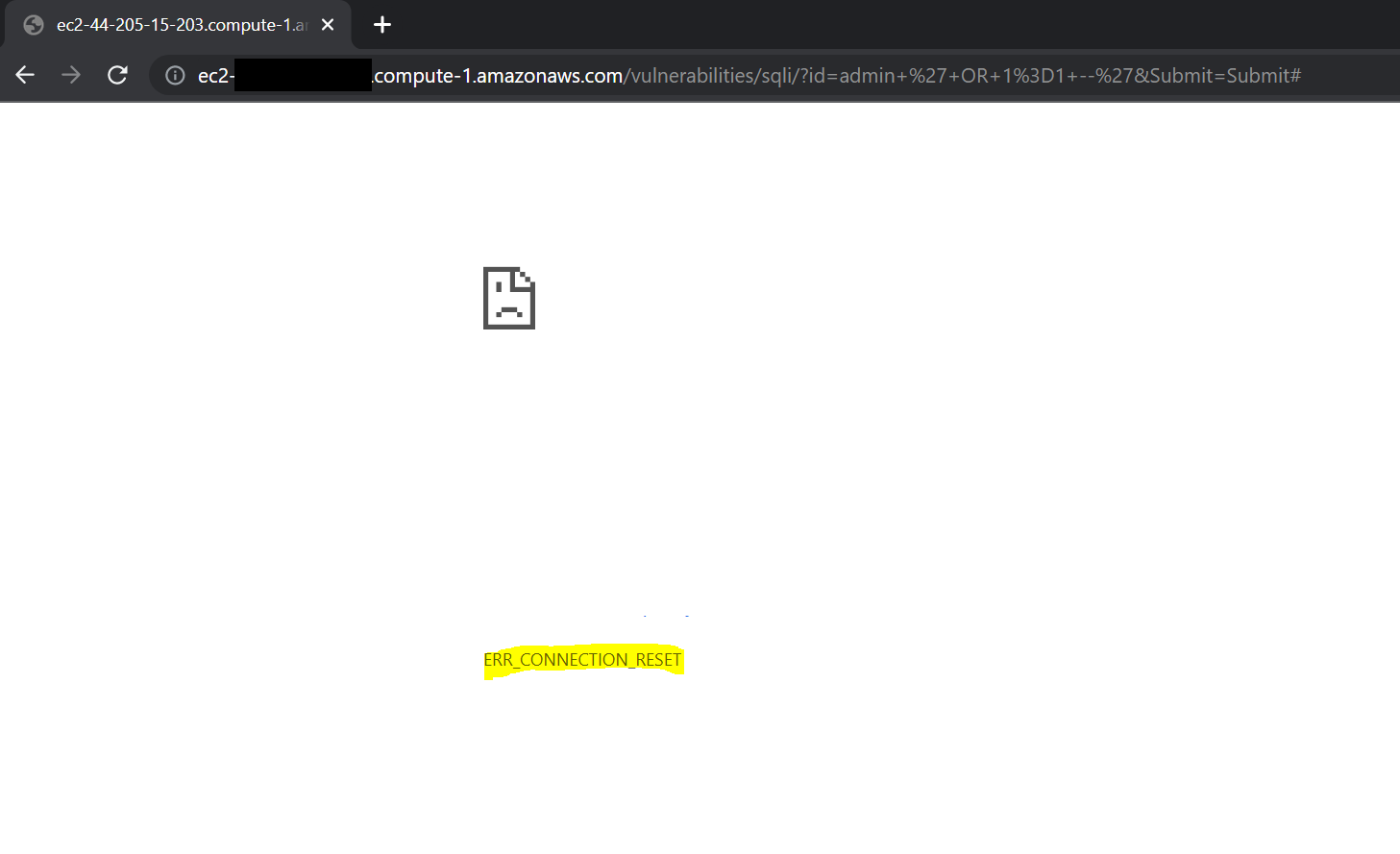
10. Repeat the SQL attack.
- Select: SQL Injection
- User ID:
admin ' OR 1=1 --' - Note that the connection has now been reset.