Creating the base AWS Environment
1. Creating the base AWS environment using AWS CloudFormation Template
You can use the CloudFormation template below to create the infrastructure in the same AZ with the 2 subnets, NAT Gateway, Internet Gateway, and EC2 instances.
2. Click on Next

3. Specifying additional stack parameters
A Key Pair is required before continuing this CloudFormation deployment. If you need help creating a Key Pair -> Create a key pair
-> CLICK HERE to see how to create a key pair
AWS Console -> EC2 -> Key Pairs -> Create key pair

-
Stack Name:
workload-security-workshop -
InspectionVPCCIDR: the CIDR that you want to use for the VPC. You don’t need to change it if you don’t want to change the default configuration.
-
KeyPair: Your KeyPair name.
-
MyPublicIP: Your public IP in CIDR. (e.g. 191.162.228.91/ 32) . You can grab it using a few tools or websites (https://ipinfo.io/ip). It will be used to only allow your IP to access the vulnerable application (DVWA)
-
ProtectedPrivateSubnetAZ: the AZ that you want to use for your Private subnet.
-
ProtectedPrivateSubnetCIDR: the CIDR that you want to use for the Private subnet. You don’t need to change it if you don’t want to.
-
ProtectedPublicSubnetAZ: the AZ that you want to use for your Public subnet.
-
ProtectedPublicSubnetCIDR: the AZ that you want to use for your Public subnet. You don’t need to change it if you don’t want to.
3.1. Stack details example:

4. Configure stack options
Leave fields as default and click Next, or optionally define tags to the environment if desired.

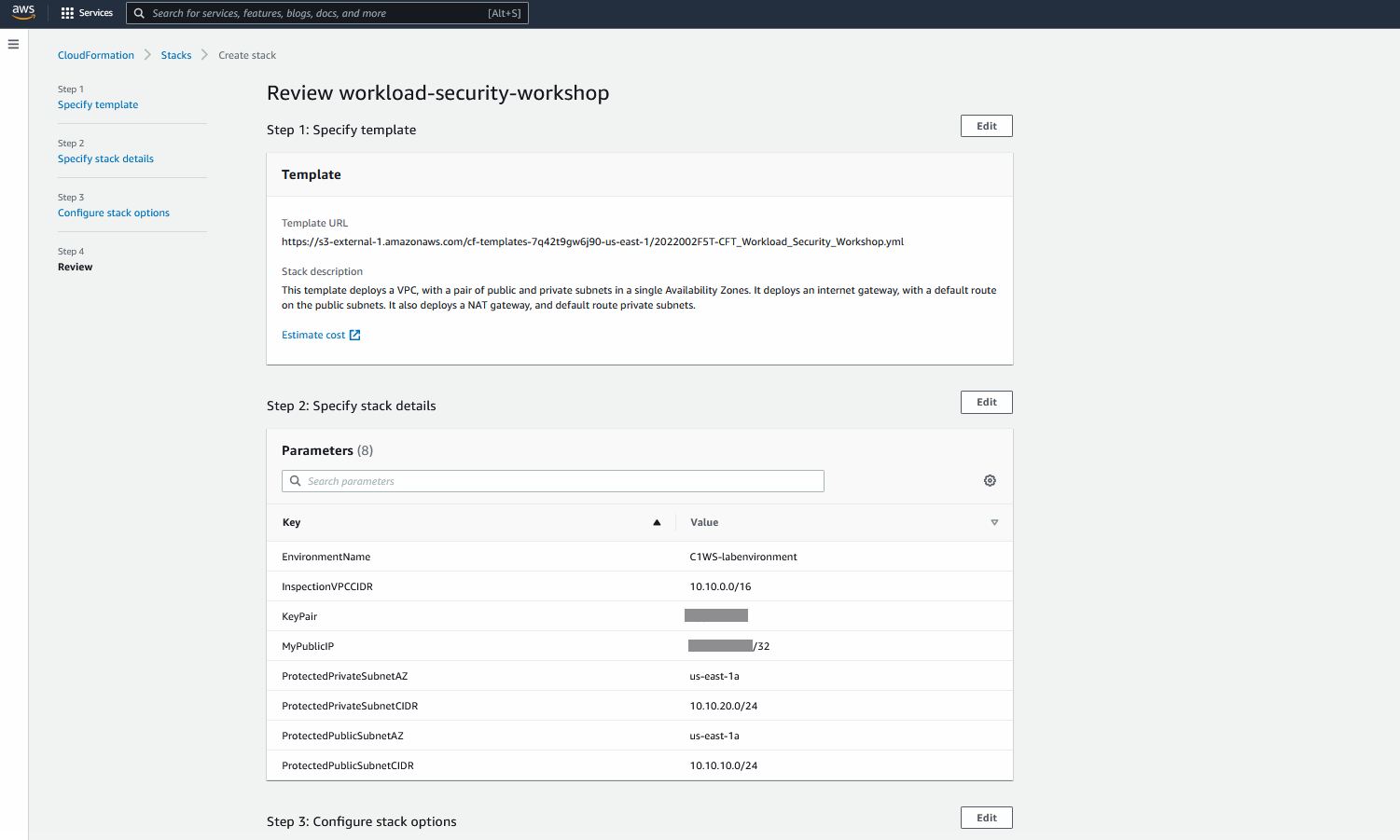
5. Review the template parameters
- Mark the checkbox the “I acknowledge… “
- Click on Create Stack


6. Follow up the events during creation of the stack.
- Select the Events tab
- Click Refresh

7. Ensure the stack status has reached Create_Complete.
- Select the Stack info tab

8. Verify your server fleet is now showing up within Cloud One Workload Security.
- Navigate to Cloud One - Workload Security.
- Click the Computers tab.
Here you get complete visibility into the server fleet status. (Optional) Even more information can be displayed by clicking columns.

Et voila, we just automated the deployment of multiple Workload Security Agents in our AWS environment 🤩 ☁️ 🤖 🚀
